It’s time to take your threat intelligence to the skies. Today’s attackers can easily contort malware and switch up their infrastructure, leaving security teams that chase attackers with static indicators and artifacts constantly feeling a step behind. While IP addresses, processes, and domains change, there is an underlying set of stealthy attacker techniques that foreshadow every successful breach.
At Rapid7, we see a constant stream of threats, from the Metasploit project, our Managed Detection and Response customers, and incident response and penetration testing engagements. During threat investigations, our expert analysts zero in on these stealthy techniques, while researching the attacker’s targets and goal. This intelligence is crafted into Attacker Behavior Analytics (ABA) detections, which can find malicious behaviors even if they have been altered to evade prevention defenses.
[Webcast] Getting the Knack of ATT&CK
Learn how your organization can utilize MITRE ATT&CK framework in this on-demand webcast.
Watch NowAttacker Behavior Analytics Library
Below is a list of released ABA detections, all of which come with our threat detection solution, InsightIDR, and automatically match against your data in real time. This is threat intelligence that moves at the speed of the attacker—if a new exploit comes out, our team will craft a detection, test it against the Rapid7 platform, and deploy it in InsightIDR—all within hours. Still craving that aged, open-source threat feed now?
-
Office 365 Spearphishing Campaigns
Verticals targeted: All
Office 365 Spearphishing Campaigns
Verticals targeted: AllRecent threat actors are targeting Microsoft 365 credentials with spearphishing campaigns. Attacker behavior analytics have been released that detect the dynamically generated phishing URLs used in these campaigns.
For more information, reference our public blog post released by Rapid7's Managed Detection & Response (MDR) team on Aug 20: http://blog.drordi.com/2019/08/20/how-attackers-can-harvest-users-microsoft-365-credentials-with-new-phishing-campaign/
Detections added to InsightIDR: Threat intelligence and detections for relevant spearphishing URLs.
-
Mshta Used to Evade Prevention Defenses
Verticals targeted: All
Mshta Used to Evade Prevention Defenses
Verticals targeted: All
Macros are small Visual Basic for Applications (VBA) embedded inside of Microsoft Office documents, such as Powerpoint, Excel, Word, and Publisher. Macros are often used maliciously to run commands using a number of possible built-in Windows utilities, such as mshta.exe, to download malware and compromise the system. Malicious documents are often sent via phishing emails.
For more information on the technique, see T1170 of MITRE ATT&CK: http://attack.mitre.org/techniques/T1170/.Detections added to InsightIDR: 4, to detect anomalous Mshta execution and activity
-
Hidden Cobra
Verticals targeted: All
Hidden Cobra
Verticals targeted: All
DHS and the FBI track actors out of North Korea under the name Hidden Cobra, also known as the Lazarus Group. These actors have been responsible for a wide range of malicious activities, including WannaCry and the Sony hack. Their motivations are financial gain, espionage, and national interests. Rapid7 tracks several malware families related to Hidden Cobra, including:
- KEYMARBLE, a remote access trojan being used by North Korean entities that is capable of accessing device configuration data, downloading additional files, executing commands, modifying the registry, capturing screen shots, and exfiltrating data.
- Typeframe, a trojan being used by North Korea state-sponsored cybercriminals. This family consists of 32-bit and 64-bit Windows executable files, as well as a malicious Microsoft Word document that contains Visual Basic for Applications (VBA) macros. According to their research, these files are capable of downloading and installing malware, installing proxy and remote access trojans (RATs), connect to command control (C&C) servers to receive instructions, and alter the victim's firewall to allow incoming connections.
Detections added to InsightIDR: 23, for KEYMARBLE and Typeframe trojans.
-
Leafminer
Verticals targeted: Government
Leafminer Attack Group
Verticals targeted: Government, businesses
Symantec has uncovered the operations of a threat actor named Leafminer that is targeting a broad list of government organizations and business verticals in various regions in the Middle East since at least early 2017. The group tends to adapt publicly available techniques and tools for their attacks and experiments with published proof-of-concept exploits.
Detections added to InsightIDR: 54, all related to the Leafminer attack group IOCs identified by Symantec.
-
Luoxkep Campaign
Verticals targeted: All
Luoxkep Campaign
Verticals targeted: All
Malicious campaign identified by 360 Safe that is exploiting CVE-2018-2893 for cryptomining and DDoS attacks.
Detections added to InsightIDR: 3, for downloads, domains, and IPs related to Luoxkep.
-
Remote Desktop Brute-Force Attempt IPs, Existing ABA Updates
Verticals targeted: All
Remote Desktop Brute-Force Attempt IPs
Verticals targeted: All, utilized via legitimate Windows protocolRemote Desktop Protocol (RDP) is a legitimate protocol used for remote management of Windows systems, however it is often abused by attackers to gain access and control of systems. One way attackers gain access is by brute forcing RDP passwords. This threat identifies all source IPs seen to authenticate more that 50 times against RDP across ALL Lorelei honeypots during the previous day.
Detections added to InsightIDR: 20, which identify IPs authenticating against RDP across Lorelei honeypots.
_______________________________________________________________________
Updates and Additions to Existing ABA Threats:
Malicious Document Threat: 1 new behavior added — Word Spawns Executable from Users DirectoryMalicious PowerShell: 2 new behaviors added — Obfuscated Script and Download Cradles
Privilege Escalation: 2 new behaviors added — UACMe Privilege Escalation Tool, Company Name in Binary Metadata; and UACMe Privilege Escalation Tool, Original Name in Binary Metadata
Credential Theft: 4 new behaviors added — Mimikatz Flats (DumpCreds or DumpCerts), Mimikatz Sekurlsa, Mimipenguin, and Hashcat
-
Thrip Attack Group, Remote Admin Tools
Verticals targeted: Communications, defense contractors, others
Thrip Attack Group
Verticals targeted: Telecommunications, satellite communications, mapping and geospacial imaging, defense
Thrip is an adversary group identified by Symantec that they have been tracking since 2013. This adversary group focuses on espionage activities, primarily targeting telecommunications, satellite communications, mapping and geospatial imaging, and defense contractors in the United States and Southeast Asia. They use a combination of malware and other tools such as PSExec and Mimikatz to compromise and move through systems, identifying and exfiltrating information.Detections added to InsightIDR: 123, which identify activity around specific trojans and backdoors.
_______________________________________________________________________
Remote Admin Tools
Verticals targeted: AllAn attacker may use legitimate remote access software, such as Ammyy Admin, to create a command and control ability to target systems. These services are commonly used as legitimate technical support software and may be whitelisted in an environment. Admin tools such as Ammyy Admin are commonly used by attackers, as seen by the Rapid7 MDR SOC.
Detections added to InsightIDR: 3, which look for the presense of Ammy Admin.
-
VPNFilter
Verticals targeted: All
VPNFilter
Verticals targeted: All
VPNFilter is a new modular malware tracked by Cisco's Talos group. This malware has been primarily targeting home and small business routers, namely MikroTik, Netgear, Linksys, and QNAP network storage devices. This malware can be used for website credential theft and data collection, and has a destructive capability where the firmware can be destroyed, thus causing the device to be unusable.Detections added to InsightIDR: 51, which identify specific indicators related to VPNFilter activity.
-
Malicious PowerShell
Verticals targeted: All
Malicious PowerShell
Verticals targeted: AllPowerShell is an interactive command-line interface and scripting environment included in the Windows operating system. Adversaries can use PowerShell to perform a number of actions, including discovery of information and execution of code. These are behaviors that are commonly used by attackers, as seen by the Rapid7 MDR SOC.
Detections added to InsightIDR: 10, which identify specific behaviors related to malicious PowerShell activity.
-
Valyria Downloader, OilRig
Verticals targeted: All
Valyria Downloader
Verticals targeted: All, presents as phishing emailThe Valyria Downloader is a trojan that is sent via phishing emails, often using "invoice overdue" or "outstanding payment" themed emails. Once the emails are opened, the downloader will initiate a connection to a command and control domain to download additional files, typical associated with the URSNIF data-stealing malware family.
Detections added to InsightIDR: 9, which identify hashes related to the downloader installation and malicious documents, and the use of Powershell spawning process out of Users/Public/Documents.
_______________________________________________________________________
OilRig
Verticals targeted: AllOilRig is a threat group tracked by Palo Alto Labs' Unit 42. They primarily target organizations in the Middle Eastern region, however, this group has targeted organizations outside of the Middle East as well. OilRig often leverages the trust relationship between organizations to attack their primary targets. The OilRig threat group overlaps with APT 34.
Detections added to InsightIDR: 9, which identify malicious credential harvesting domains and a tactic where an adversary dumps credentials from the command line, often seen with Mimikatz.
-
Satan Ransomworm, Orangeworm
Verticals targeted: Healthcare, manufacturing, agriculture
Orangeworm Attacks
Verticals targeted: Healthcare, manufacturing, agriculture
Symantec has identified an attack group named Orangeworm, who are deploying the Kwampirs backdoor in a targeted attack campaign against the healthcare, manufacturing, and agriculture sectors, as well as information technology companies who support these industries. This attack group and malware are both noisy and do not try to hide their activity, relying primarily on their targeting of older devices that are often not well monitored.Detections added to InsightIDR: 43, which identify dropper and payload hashes, along with connections to command & control IP addresses.
______________________________________________________________________
Satan Ransomware
Verticals targeted: None, offered as ransomware-as-a-serviceSatan Ransomware appeared in early 2017 and was one of the original "Ransomware as a Service" offerings on dark websites. The ransomware is spread via phishing emails or malicious links, and has recently been updated to include the EternalBlue SMB exploit for spreading within a network.
Detections added to InsightIDR: 6, which identify variants of the Satan ransomware and dropper, the EternalBlue SMB exploit, and suspicious associated command line activity.
-
Fauxpersky, SamSam
Verticals targeted: Healthcare, government, education
Fauxpersky Keylogger Malware
Verticals targeted: None, spreads via USB drives
Fauxpersky is a new keylogger malware disguised as Kaspersky antivirus. The malware is based on the AutoHotKey app, which lets users write codes to automate tasks. Researchers say that the malware is highly efficient, self propagating, and persistent. It infects Windows PCs by spreading through USB drives and then replicates to all the drives on the machine. Fauxpersky then collects data using Google Forms, sends that data to the attackers' inbox, and deletes the original data from the drive.Detections added to InsightIDR: 6, which identify variants of the Fauxpersky malware.
_______________________________________________________________________
SamSam Ransomware
Verticals targeted: Healthcare, government, educationSamSam Ransomware is a ransomware variant used by a group tracked as the SamSam Group or Gold Lowell. This group will gain access to the target, often using RDP access or scanning for server-side vulnerabilities, and then deploy their ransomware variant. SamSam is targeted, the actors will often focus on a particular industry or vertical and target organizations within that vertical before moving onto a different focus.
Detections added to InsightIDR: 7, which identify variants of the SamSam ransomware, as well as Shadow Copy deletion, a common ransomware behavior to thwart recovery efforts.
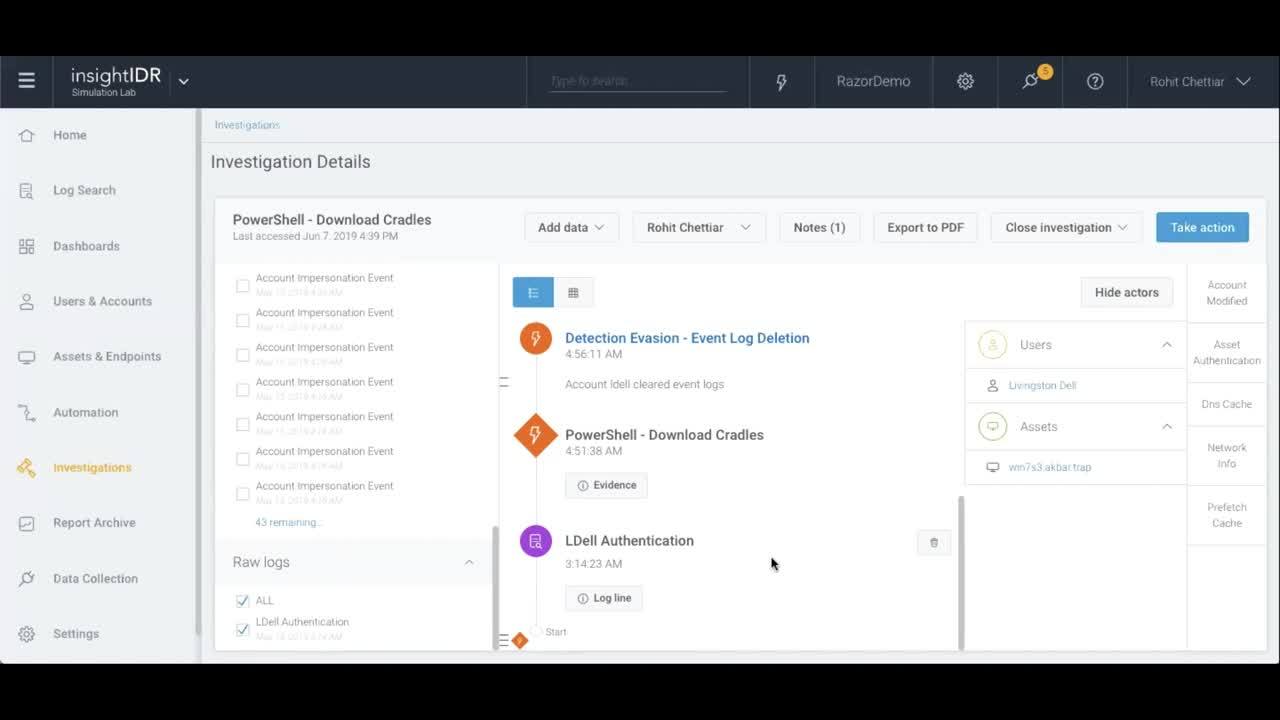
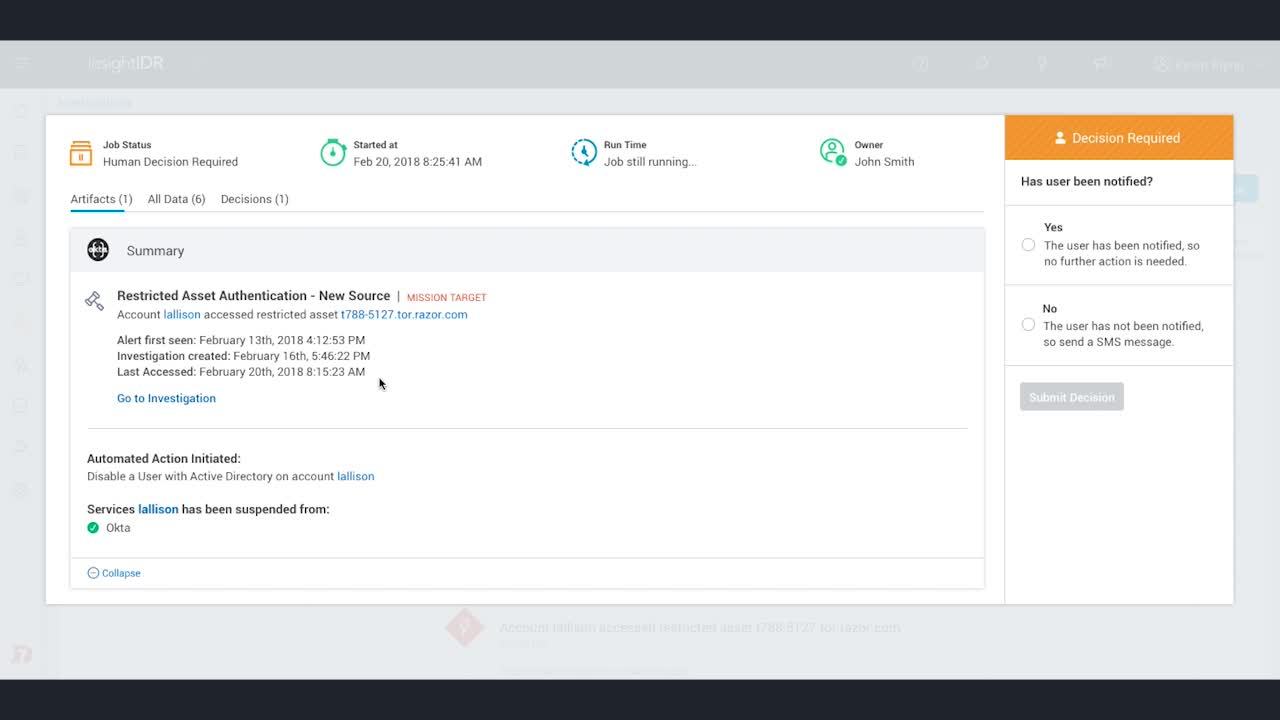
Attacker Behavior Analytics in Action
See how attacker behavior is detected in InsightIDR, and learn more about our cloud SIEM.
Investigating PowerShell and Mimikatz Activity with InsightIDR
Learn how InsightIDR detects attacker behavior that uses PowerShell to download executables from the internet.